A botched home invasion in the Paris suburbs on Feb. 12 marked a tactical shift in crypto’s physical-threat or “wrench attack” landscape.
The target, according to French media reports, was the CEO of Binance France. Binance confirmed an employee was targeted and said the employee and family are safe.
Two phones were stolen before the suspects were arrested at Lyon Perrache station. The assailants reportedly entered the wrong residence first before moving to their intended target. This detail suggests reconnaissance and intent, not opportunism.
The incident is more concerning than the rising baseline of wrench attacks.
This was a named executive at a recognizable institutional brand, the largest crypto exchange by trading volume.
The attackers were comfortable hunting a figure tied directly to a corporate chart, not just a wallet balance.
That comfort signals a new phase: organized criminals have elevated crypto coercion into a structured, coordinated line of work.
They are professionalizing target selection, with France emerging as the clearest example of this shift.
Record-breaking “wrench attack” wave
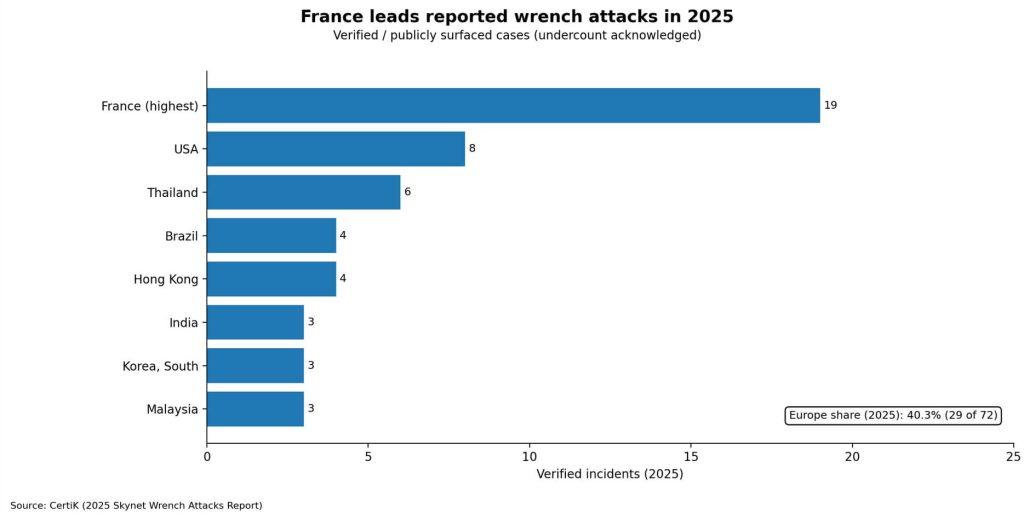
CertiK’s 2025 Wrench Attacks Report logged 72 verified physical coercion incidents globally, a 75% increase over 2024, with confirmed losses exceeding $40.9 million.
The firm explicitly notes this figure undercounts the true scale, as many victims don’t report, and some incidents never surface publicly. Europe accounted for 40.3% of all attacks, and within Europe, France led with 19 verified cases.
The brutality mix is shifting. Kidnapping became the dominant vector in 2025, with 25 incidents globally. Physical assaults surged 250% year-over-year, rising from four cases in 2024 to 14 in 2025.
The tactics are diversifying: home invasions, street abductions, and family targeting. Criminals are treating physical coercion as a repeatable business model with predictable returns, and the data shows they’re iterating on methods that work.
Early 2026 has maintained the France-heavy pattern. Tracking by Jameson Lopp and coverage across French and international outlets document a disproportionate concentration of cases in French jurisdictions.
The Binance France incident fits the trend, but it also extends it. Executives were rarely the primary target category until now.
Why executives change the calculus
Targeting an exchange CEO introduces variables that retail whale-hunting doesn’t.
Executives are assumed to hold three things that make them high-value marks: personal holdings, privileged system access, and wealthy networks.
Whether those assumptions are accurate is irrelevant. What matters is whether criminals believe they are.
CertiK explicitly frames the evolution: attacks have moved from opportunistic crime to organized, OSINT-driven operations. Finding a CEO’s home address is easier than finding a pseudonymous whale’s cold storage location. Corporate records, LinkedIn profiles, conference speaker lists, and real estate filings create a discoverable attack surface.
The perceived payout is larger and faster. An executive can unlock institutional resources or leverage them to meet ransom demands that exceed what any individual could pay.
The attack surface extends beyond the executive. Reuters’ coverage of French incidents shows abductors targeting relatives, such as CEOs’ daughters and fathers of founders, because coercive economics favor soft targets over hardened ones.
A family member at home is easier to intercept than a security-conscious principal, and the leverage is equivalent.
Why France became the “wrench attack” hotspot
France’s dominance in wrench attack statistics isn’t random. Five structural factors converge to make it uniquely vulnerable.
First, France hosts a dense, visible crypto founder class. Ledger is headquartered in Paris. Paymium is one of Europe’s oldest exchanges. Multiple high-profile figures and entities are publicly associated with French addresses, creating a target-rich environment for criminals who do basic research.
Repeated cases show attackers targeting identifiable figures and their relatives, suggesting that name recognition drives target selection.
Second, doxxing and data availability create mapable targets. The Wall Street Journal documented how data leaks and public records expose addresses, turning an abstract “crypto user” into a concrete “person at this location.”
In January 2026, hackers breached Waltio, a French crypto tax software provider, reportedly obtaining emails and tax reports tied to roughly 50,000 users.
French authorities are investigating. Linking identity, crypto activity, and location is exactly what turns surveillance into operational targeting.
More explosive is the reported allegation, still under investigation, that a French tax office employee sold sensitive lookup results about crypto investors.
French media describe the case as an active prosecution. If substantiated, it suggests criminals had direct access to government-held identity and financial data.
Third, organized kidnapping infrastructure appears to be repeatable and coordinated. Le Monde’s reporting describes structured gang models across multiple kidnappings, including remote coordination and operations linked to Morocco.
This isn’t amateur crime, but crew-based work with logistics, division of labor, and cross-border components. Once that infrastructure is in place, it scales.
Fourth, regulatory compliance concentrates sensitive identity data in areas that are vulnerable to leaks. France operates under the AMF’s DASP/PSAN framework and is actively messaging the MiCA transition deadline of July 1.
Compliance requirements such as the “travel rule” require identity collection and data sharing.
Reuters quoted French industry voices criticizing these mandates, arguing they increase exposure.
Greater compliance means more identity data across more databases, and each database is a potential breach surface.
Fifth, copycat dynamics and media feedback loops amplify successful tactics. Once a jurisdiction is seen as “working” for criminals, attacker playbooks spread.
More dedicated crews emerge. Victims adjust their behavior by hiring bodyguards, reducing public presence, and compartmentalizing holdings.
However, those adjustments fail to eliminate the threat and instead increase the cost of defense, even as attackers shift their focus to the next vulnerability.
| Structural factor | How it increases wrench risk | Concrete proof point | Forward-looking implication |
|---|---|---|---|
| Visible founder/executive density | Easier OSINT targeting | Ledger (Paris) + Paymium CEO family targeted in French cases | Execs become a target category, not an exception |
| Doxxing + public records | Addresses become “actionable” | WSJ: leaks + public records can expose home addresses | Target discovery rate rises as datasets accumulate |
| Waltio breach (Jan 2026) | Identity + tax + activity linkage | Reported breach tied to ~50,000 users (emails + tax reports) | A breach becomes a targeting map |
| Organized crews / repeatable operations | Scalable kidnapping logistics | Le Monde: structured gang model, remote coordination, Morocco link | Crime becomes a pipeline (repeatable playbook) |
| Compliance data concentration (travel rule / PSAN) | More identity databases | Reuters: French industry voices warn “travel rule” identity/data collection increases exposure | More databases = more breach surfaces (and higher leak risk) |
What happens next
The near-term scenario is hardening without solving.
More executives will adopt personal security, reduce visibility, and move assets into compartmentalized custody. Attacks will continue because the expected value remains high and the attack surface continues to grow.
CertiK describes the threat as “structural,” meaning it’s embedded in incentives rather than a transient crime wave.
A France-specific inflection could arrive if the Waltio breach and the tax official allegations trigger stricter rules on access logs, identity minimization, and breach liability.
If regulators impose real penalties for data exposure and limit who can query sensitive records, France could reduce its target-discovery rate. That would require treating data handling as a security problem, not just a compliance checkbox.
The crypto irony scenario involves institutional custody making a comeback. If wealthy users and executives conclude that self-custody increases physical risk, they may shift toward professional custody services with insurance and institutional-grade security.
That reduces wrench attack ROI, but it re-centralizes custody and changes the threat model back toward cyber compromise and institutional vulnerabilities.
Chainalysis has flagged rising emphasis on individual targeting and noted links between theft patterns and market conditions, suggesting coercion incentives track price cycles.
The stakes are institutional now
The Binance France incident signals that exchange executives have become high-value targets. Criminals view them as worth the risk.
That belief reshapes the security posture for every crypto company with a public-facing team and a French presence. It also reshapes recruiting: how many qualified professionals will accept roles that come with kidnapping risk?
France’s regulators and law enforcement face a decision. They can treat these incidents as isolated crimes and rely on arrests after the fact.
Or they can recognize that data pipelines, compliance mandates, and public registries are creating systematically exploitable vulnerabilities.
The wrench attack wave reflects what happens when crypto holders are made visible, legible, and locatable at scale.
The criminals have already professionalized. The question is whether the defenses will.
The post Binance employee hunted down in botched France home invasion as crypto “wrench attack” spike spreads appeared first on CryptoSlate.